They click the link to your website, only to find that rather than your own branding and solution portfolio, they are met with pages full of content that’s irrelevant at best, or in a worst-case scenario, illegal or harmful.
That all-important first impression is instantly ruined, which can be difficult or impossible to undo. So, how can you minimise the risk of bad actors taking over your domain names? First of all, it’s important to understand how they do so – by exploiting dangling DNS records.
What is DNS dangling?
Let’s start with some fundamentals…
Domain Name System (DNS) is a protocol that automatically translates memorable domain names (like xpertex.com!) into numerical IP addresses.
A Canonical Name (CNAME) is a type of DNS database record that acts as an alias for another domain, pointing to separate, ‘canonical’ domain instead of an IP address. It indicates that a domain name is actually an alias (or nickname, if you prefer) for another domain.
When DNS records point domain names to other domains in this way, when one of those domains is abandoned, that DNS record is left dangling. And unfortunately, this means it can be hijacked to gain access to a network, where the bad actor can then begin a range of insidious activities, particularly subdomain takeover. Far from just an intrusive nuisance, this will typically lead to:
- Data Theft: Attackers can access sensitive information flowing through the subdomain, which can then be sold or held to ransom.
- Phishing and Scams: The legitimate appearance of the subdomain can be used to conduct phishing attacks.
- Malware Distribution: The subdomain can serve as a platform for distributing malware.
- Reputation Damage: An organisation’s reputation can suffer significant harm through the misuse of its subdomain, as shown in the scenario we opened this article with.
How does DNS dangling occur… and how can you avoid it?
DNS dangling is typically the result of a domain name being turned off, but no-one thinking to delete the CNAME, or when a DNS record points to a decommissioned Cloud resource. Even though the website in question is down, and can’t be viewed online, the dangling record can still be exploited.
Suffice to say, DNS dangling is a common security risk for organisations that regularly commission and decommission high volumes of different resources. But the good news is that avoiding security risks created by dangling DNS records is fairly straightforward, provided you are willing to implement (and enforce!) robust cyber security policies and processes that incorporate clear guidelines around the commissioning and decommissioning of IT resources, specifically:
- Regular Audits: Conduct regular audits of DNS records to ensure they point to valid and active endpoints.
- Monitoring Tools: Utilise tools that can automatically detect and alert on DNS misconfigurations or unused records.
- Communication and Collaboration: Ensure that IT and web development teams work together to keep track of changes in hosted services.
Remember, in spite of the advances we continue to make in cyber security, human error remains the leading cause of data breaches, so don’t leave anything to chance! Make sure world-class systems and processes go hand-in-hand with a deep awareness of each individual employee’s responsibility for maintaining robust security across your infrastructure. If you’re in any doubt as to how to do this, just get in touch, and our experts will advise you.
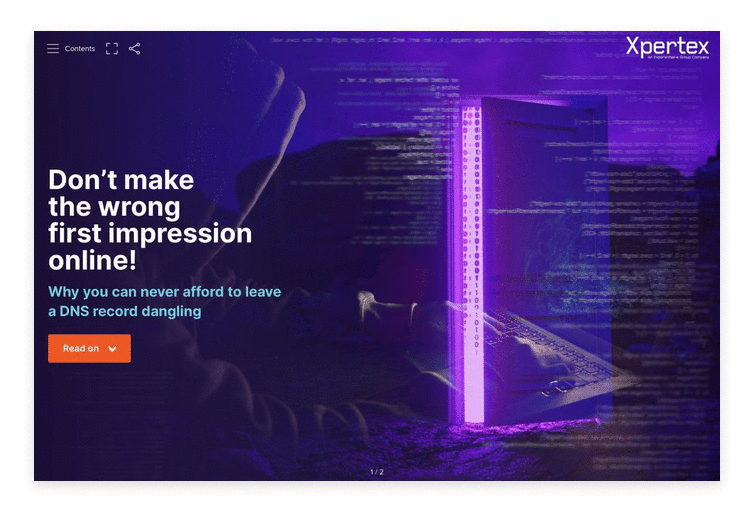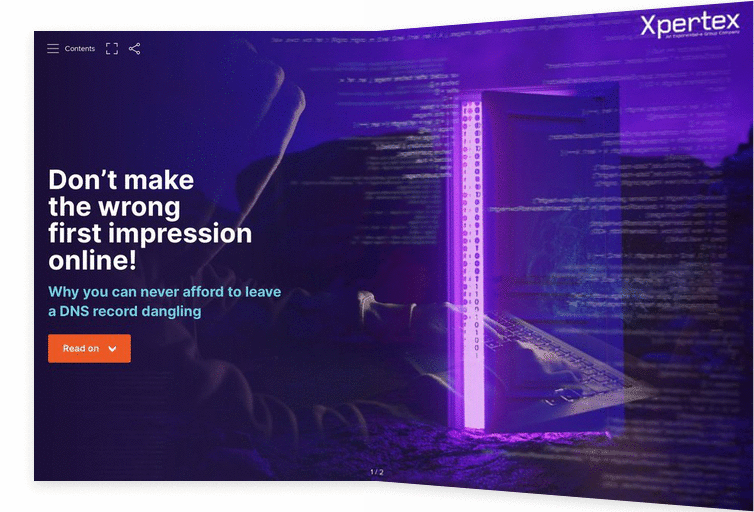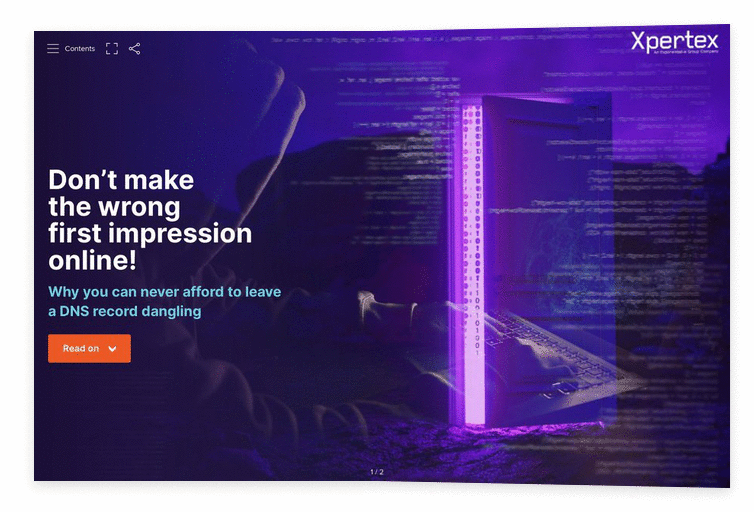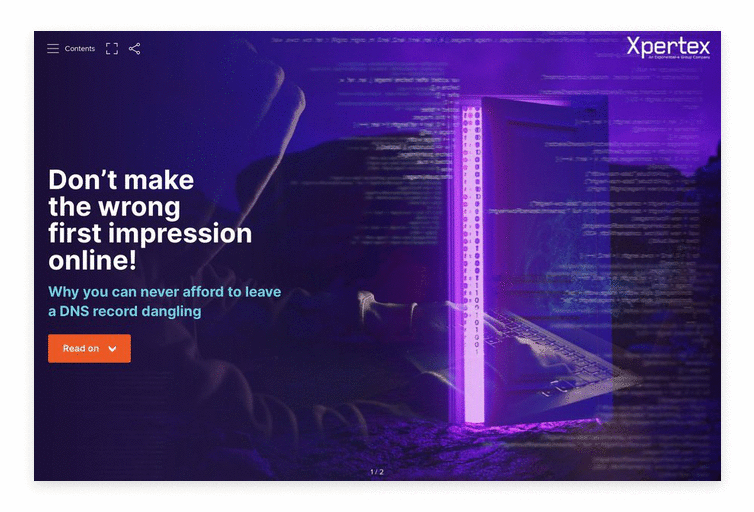
Don’t make the wrong first impression online! Why you can never afford to leave a DNS record dangling
A strong, recognisable domain name is one of the foundational elements of an organisation’s online presence, ensuring your ideal customers are able to find you as quickly as possible. Now, imagine if a customer is searching for the product or service you offer, or even for you specifically, having already decided they’re ready to engage with you.
About the author
Dean Morgan, Lead Practitioner
Dean Morgan holds a rich history spanning 30 years, where his career commences in the Defence and Intelligence Sector. For 15 years, Dean has contributed significantly as a CLAS community member, whilst also holding a membership in CiiSec. His expertise extends to conducting ISO 27001 audits, Cyber Essential Plus consultancy and executing vulnerability and risk analysis assignments for diverse external clients. All of this informs his current role as Security Consultant remaining dedicated to upholding the highest standards of cyber security.